Stay Ahead
Of Every Attack
Stay Ahead
Of Every Attack
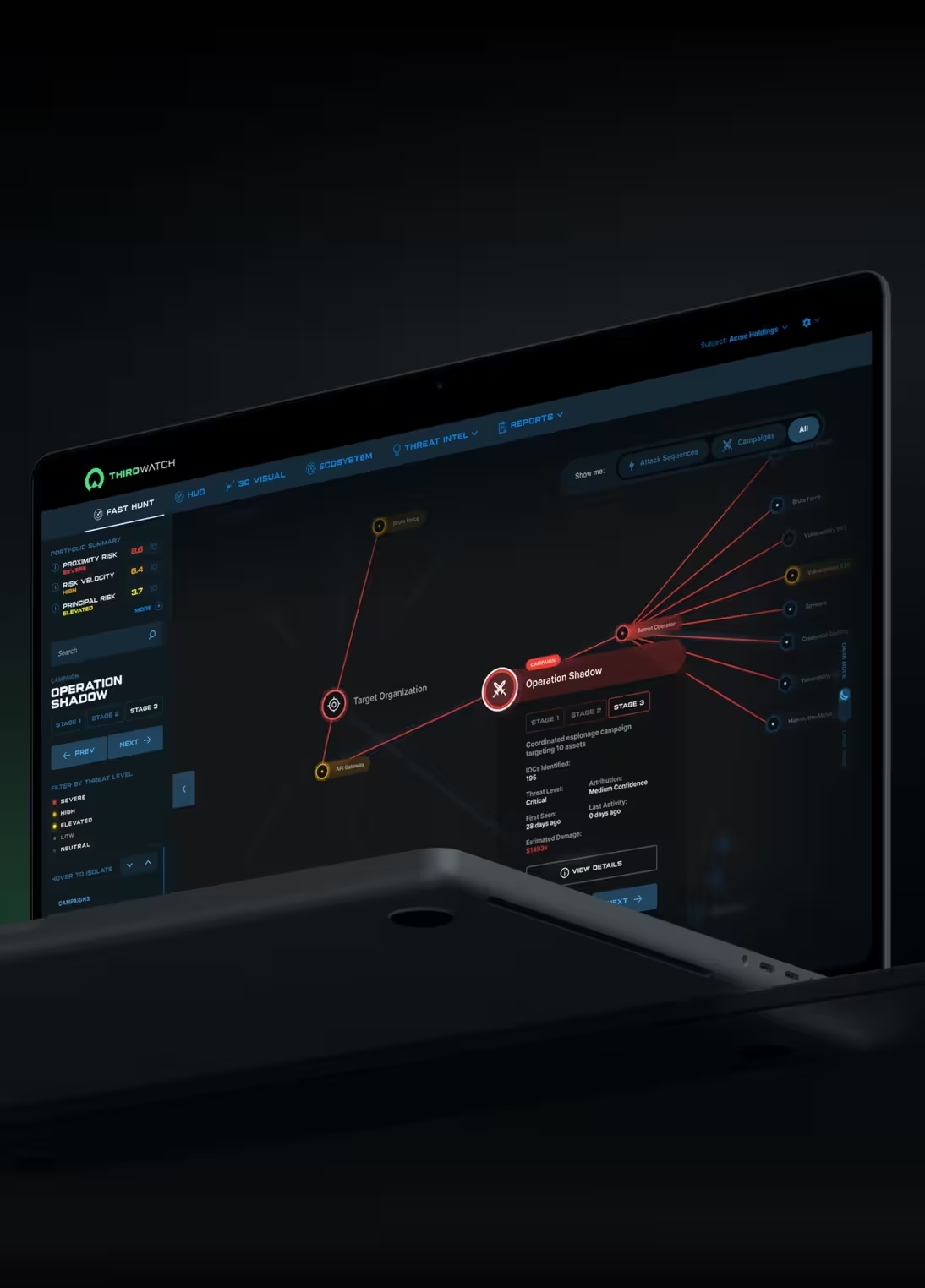
Based on zero touch, non-invasive technology, we hunt and visualize external threats surrounding your organization and your third parties, giving you critical insight and actionable intelligence needed to prevent attacks before they begin, all in 3D.

THREAT VISUALIZATION TECHNOLOGY
- Our proprietary platform delivers 3D views of external threats and 2D displays of attack campaigns, sequences and vectors, while monitoring vast networks of illicit cyber threat artifacts for a complete view of your cyber risk landscape.
4-LAYER BASELINE ANALYSIS
- ThirdWatch analyzes threats focusing on an organization, its related domains and third parties.
- The platform identifies threats developing behind legitimate infrastructure and is capable of mapping and visualizing adversarial networks.
THIRD PARTY RISK INTELLIGENCE
- Third party risk intelligence produces a comprehensive list of evidence-based threats to create a net score result.
- Enables scoring an organization's third party and supply chain risk, based on priority and operational importance.
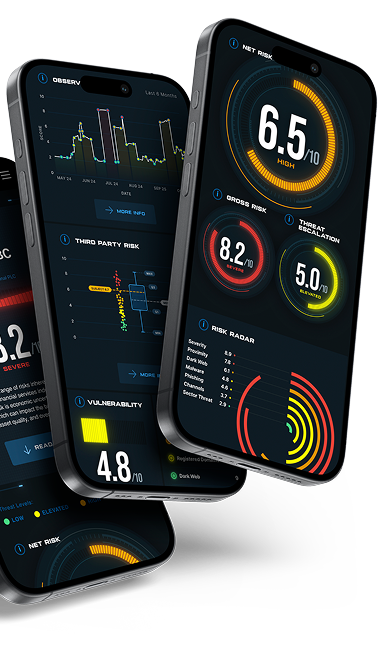
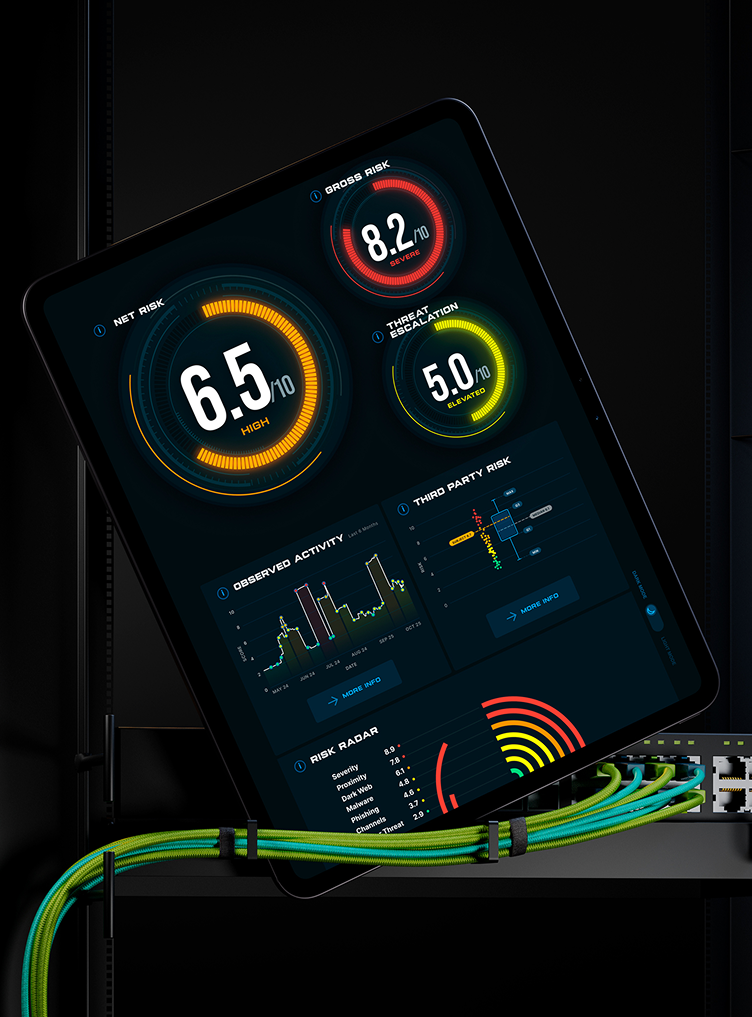
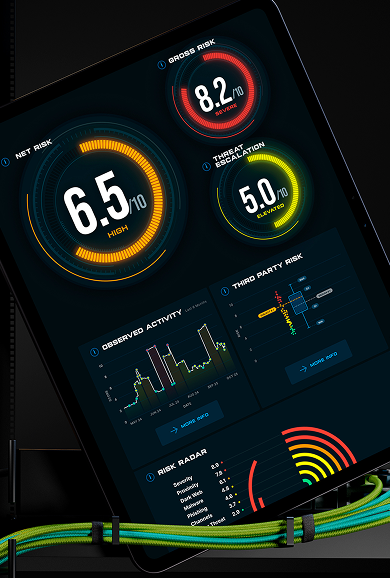
EVIDENCE-BASED SCORING
- Redefining new measures of cyber risk using AI to focus on observed activity, proximity and threat escalation.
- Our innovative scoring method delivers precise measurements that enable organizations and industries to accurately measure cyber risk.
AIM, READY, FIRE | ARFi
- The world’s first AI-driven, proactive threat-hunting methodology that neutralizes adversaries during the targeting and reconnaissance phases, before an attack can even begin.
AI–ANTICIPATED ATTACKS
- Predicting external threats before they materialize, using artificial intelligence to analyze patterns, anomalies, and intent indicators across vast data sources.
- This proactive approach helps organizations to neutralize risks in advance, reducing exposure and prevent attacks.
DIRECT THREAT INTELLIGENCE
- Curated, actionable cyber threat insights and analysis specific to an organization at global, regional, country and organizational levels.
- Ultra-scalable and ultra-fast, real time delivery of DTI to deploy directly into an organization's enterprise security stack, preventing the attack from happening.
ALERTS & REPORTS
- Delivers real-time alerts when risks are triggered across your organization, third parties, and supply chain, while generating tailored reports for boards, executives, vulnerability management, and third-party risk.
ENHANCED ATTACK SURFACE MANAGEMENT
- The industry's first enhanced Attack Surface Management Module (eASM) that maps the direct, external threats facing an organization to its known vulnerabilities produced from a vulnerability report.
- This truncates the timetable to analyze, delivers rapid prioritization and eliminates false positives.
THREAT VISUALIZATION TECHNOLOGY
- Our proprietary platform delivers 3D views of external threats and 2D displays of attack campaigns, sequences and vectors, while monitoring vast networks of illicit cyber threat artifacts for a complete view of your cyber risk landscape.
EVIDENCE-BASED SCORING
- Redefining new measures of cyber risk using AI to focus on observed activity, proximity and threat escalation.
- Our innovative scoring method delivers precise measurements that enable organizations and industries to accurately measure cyber risk.
DIRECT THREAT INTELLIGENCE
- Curated, actionable cyber threat insights and analysis specific to an organization at global, regional, country and organizational levels.
- Ultra-scalable and ultra-fast, real time delivery of DTI to deploy directly into an organization's enterprise security stack, preventing the attack from happening.
4-LAYER BASELINE ANALYSIS
- ThirdWatch analyzes threats focusing on an organization, its related domains and third parties.
- The platform identifies threats developing behind legitimate infrastructure and is capable of mapping and visualizing adversarial networks.
AIM, READY, FIRE | ARFi
- The world’s first AI-driven, proactive threat-hunting methodology that neutralizes adversaries during the targeting and reconnaissance phases, before an attack can even begin.
ALERTS & REPORTS
- Delivers real-time alerts when risks are triggered across your organization, third parties, and supply chain, while generating tailored reports for boards, executives, vulnerability management, and third-party risk.
THIRD PARTY RISK INTELLIGENCE
- Third party risk intelligence produces a comprehensive list of evidence-based threats to create a net score result.
- Enables scoring an organization's third party and supply chain risk, based on priority and operational importance.
AI–ANTICIPATED ATTACKS
- Predicting external threats before they materialize, using artificial intelligence to analyze patterns, anomalies, and intent indicators across vast data sources.
- This proactive approach helps organizations to neutralize risks in advance, reducing exposure and prevent attacks.
ENHANCED ATTACK SURFACE MANAGEMENT
- The industry's first enhanced Attack Surface Management Module (eASM) that maps the direct, external threats facing an organization to its known vulnerabilities produced from a vulnerability report.
- This truncates the timetable to analyze, delivers rapid prioritization and eliminates false positives.
Attack Surface Management
Predict. Prevent. Defeat.
The industry’s first enhanced Attack Surface Management Module (eASM) maps the direct, external threats facing an organization to its known vulnerabilities produced from a vulnerability report.
eASM accurately maps threats from an organization’s external environment to its known vulnerabilities, highlighted in an easy-to-understand report.
Clear delineation between actual threats and false positives at the click of a button.
Attack Surface Management
Predict. Prevent. Defeat.
The industry’s first enhanced Attack Surface Management Module (eASM) maps the direct, external threats facing an organization to its known vulnerabilities produced from a vulnerability report.
eASM accurately maps threats from an organization’s external environment to its known vulnerabilities, highlighted in an easy-to-understand report.
Clear delineation between actual threats and false positives at the click of a button.

3D Visualization
Clarity Through Threat Visualization
Direct Threat Risk Management (DTRM) creates a new category of cyber solutions by monitoring external threats to an organization, its related domains, and third parties. ThirdWatch identifies all illicit activities linked to the organization’s active digital footprint.


DIRECT THREAT RISK MANAGEMENT
Find Weakness Fast
ThirdWatch’s DTRM defines a new category of cyber defense by continuously monitoring external threats across an organization, its digital landscape, and third-party ecosystems. It delivers real-time visibility into illicit activity, from unauthorized communications to covert interactions, ensuring no suspicious entity goes undetected.
ThirdWatch’s DTRM defines a new category of cyber defense by continuously monitoring external threats across an organization.

THIRD PARTY ECOSYSTEM VISUALIZTION
Predict. Prevent. Defeat.
Visualize an 8-layer view of your entire third-party ecosystem with clear categorization into Tier 1, 2 and 3.
Quickly uncover relationships, assess the risks each party poses and pinpoint external threats – empowering you to mitigate third-party and supply chain vulnerabilities with precision.
AIM. READY. FIRE. (ARFi)
Hunt Before
They Strike
The world’s first AI-driven, proactive threat-hunting methodology that neutralizes adversaries during the targeting and reconnaissance phases, before an attack can even begin.
DIRECT THREAT INTELLIGENCE (DTI)
Intelligence Before Impact
The world’s first, curated, client-specific, actionable intelligence isolating attack campaigns, sequences and unknown attack vectors, orchestrated via secure API into your security stack to block attacks before they occur.