Our Biggest Competitor is
the Adversary
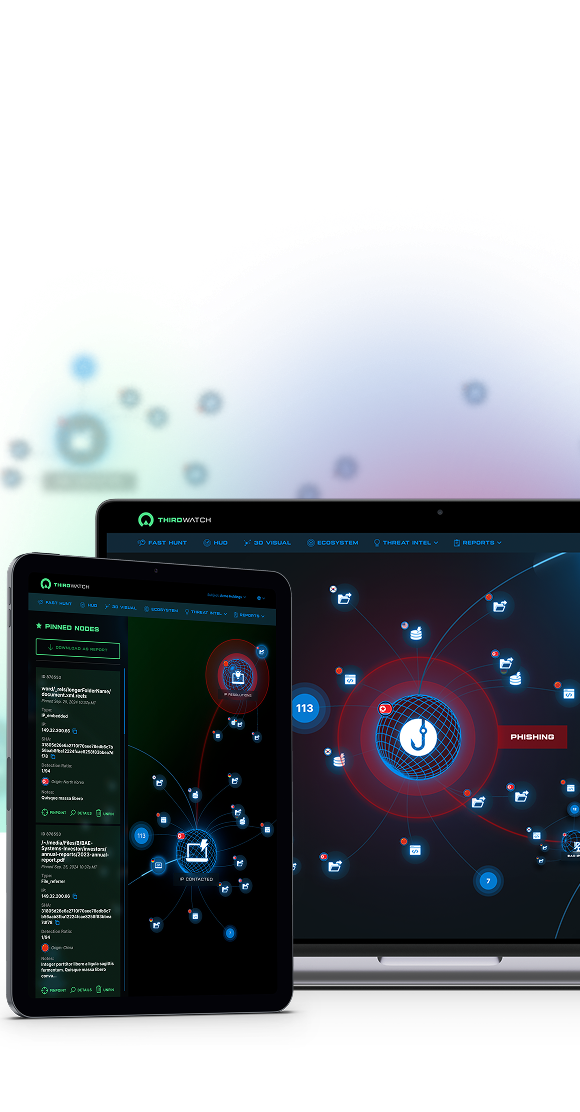

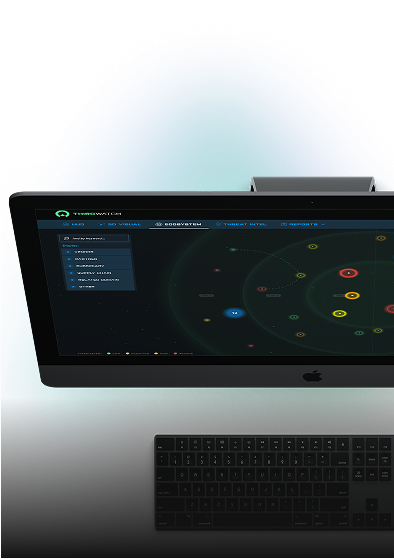
Our Edge ThirdWatch – A 3D Cyber Threat Visualization Platform. The first of its kind, ThirdWatch visualizes direct threats to your organization and your third parties.
Meet the world’s first proactive cyber defense platform. Based on zero touch, non-invasive technology, we hunt and visualize external threats surrounding your organization and your third parties, giving you critical insight and actionable intelligence needed to prevent attacks before they begin, all in 3D.
ThirdWatch is the only cyber security platform capable of producing Direct Threat Intelligence (DTI), i.e. cyber threat insights and analysis specific to an organization at global, regional, country and organizational levels.
ThirdWatch achieves pinpoint accuracy in identifying attack campaigns, sequences and unknown vectors. ThirdWatch also identifies zero detection malware and ransomware.
Our Products
We combine technology and human ingenuity, molding innovative concepts into practical, robust platforms.

Predict. Prevent. Defeat.
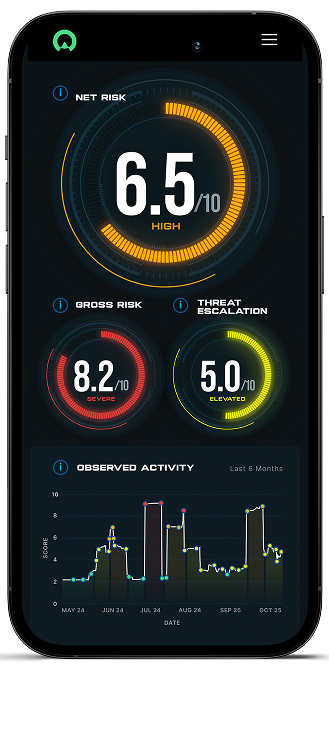
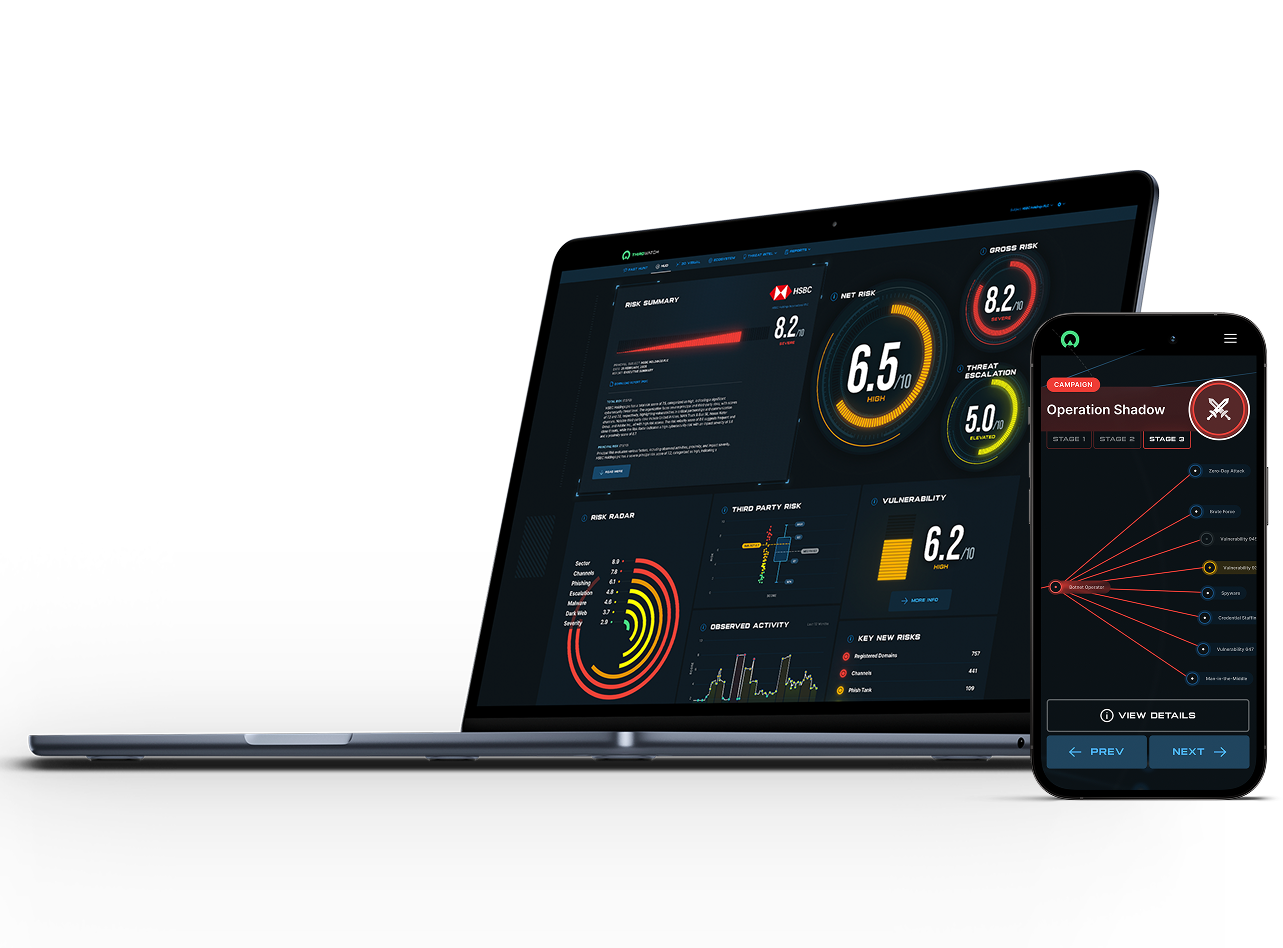
The industry’s first enhanced Attack Surface Management Module in ThirdWatch maps the direct external threats facing an organization to its known vulnerabilities in a standardized format for rapid prioritization and elimination of false positives.
Clear delineation between actual threats and false positives at the click of a button.

Predict. Prevent. Defeat.
The industry’s first enhanced Attack Surface Management Module in ThirdWatch maps the direct external threats facing an organization to its known vulnerabilities in a standardized format for rapid prioritization and elimination of false positives.
Clear delineation between actual threats and false positives at the click of a button.

We turn the world’s darkest threats into your strongest defense.

ThirdWatch

Zero Day Live

Blockwired
“Without preemptive cybersecurity, no organization is safe.The increasing speed, sophistication and scope of AI-enabled threats is destroying the reliability of existing stand-alone detection and response (DR) cybersecurity methods."
Gartner
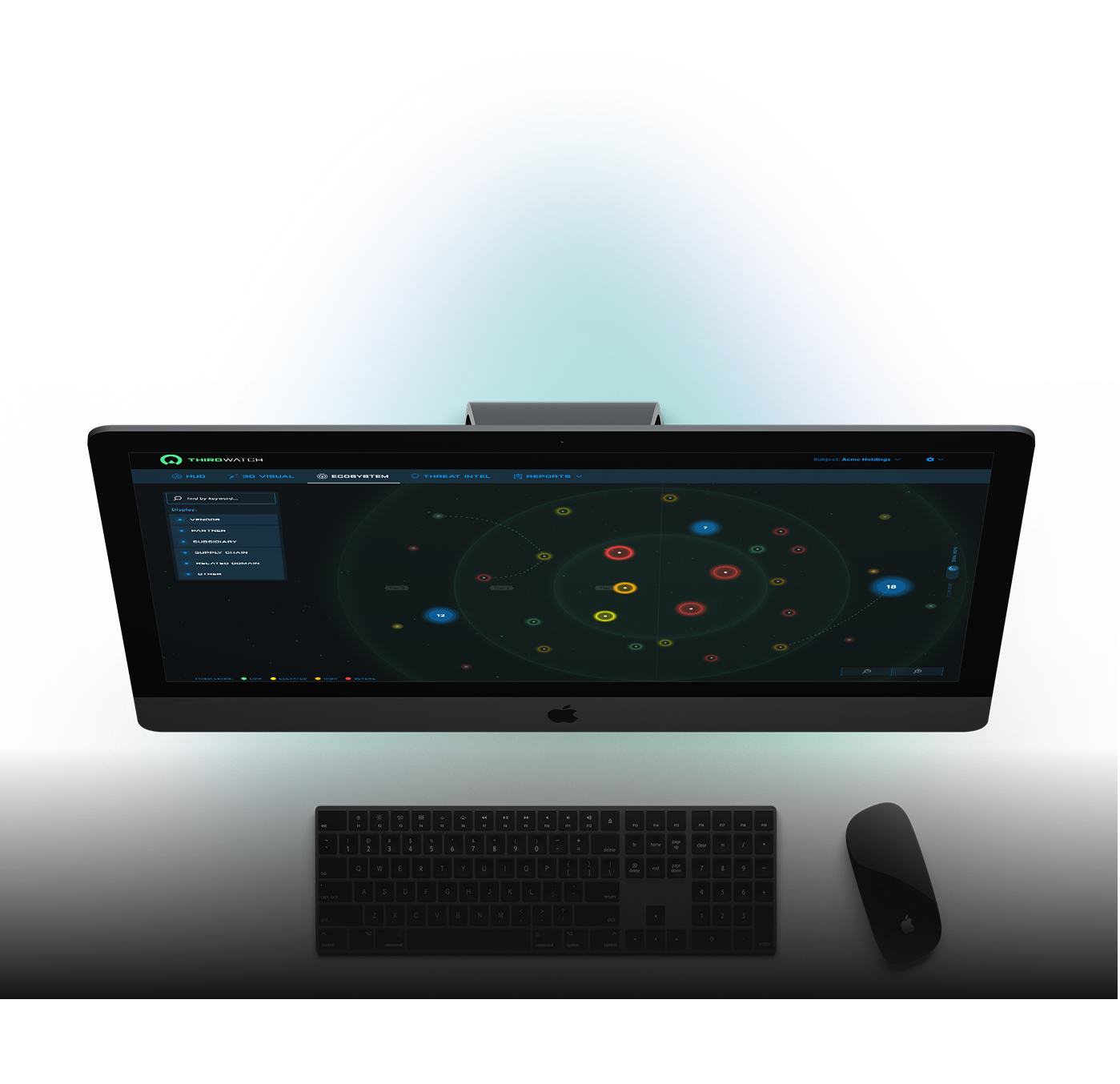
Markets we Serve
Your Industry. Our Shield.
Managed Service Providers
Financial Institutions
Retail
Manufacturing
Critical Infrastructure
Government
Telecomminucations
Digital & Technology
Life Science
Defense
Testimonials
Trusted by Industry Leaders
“We needed a strong solution to our threat intelligence requirements focusing on our Asia-Pacific operations. Blackwired proved its capability in the region to provide clear insights and hard to find intelligence that bolsters our threat intelligence program in the region”
Director of Threat Intelligence
Global Enterprise Bank | North America
“We were in the market for a solution that could not only provide threat intelligence to our enterprise but to that of our global footprint of subsidiaries. Blackwired’s ThirdWatch beat the competition hands down. It’s new ARFi technology blew us away. We were sold in the first demonstration.”
CISO
Enterprise Retail | Asia-Pacific
“Blackwired is turning the tide against the adversaries. ThirdWatch has completely changed our mindset and approach to how we process intelligence and view the cyber threat landscape. We are now at a vantage point, steps ahead of the adversary.”
Director, Threat Intelligence
Financial Institution | Middle East
Breach Watch
Trends & Tactics in Cybersecurity

AI
Jul 12, 2025
Flaw in Gemini CLI AI coding assistant allowed stealthy code execution

AI
Jul 12, 2025
Flaw in Gemini CLI AI coding assistant allowed stealthy code execution
